Wireshark-users: Re: [Wireshark-users] Question about seeing Latency in TCP conversations
Hi John,
You have almost got there, but not quite. In the variable field where you have put "time" you need to put a variable that will make sense. Unfortunately "time" I think is actually a protocol, and probably not relevant. If you open up the "Frame" section of the Packet Details of a packet, you will see a number of relevant time variables. In your case I would choose "frame.time_delta_displayed". (You can find out the variable name by selecting the relevant field, and looking in the status bar.)
You can then use this in your IO graph.
Don't forget for TCP streams you can also use TCP Stream Graphs available under the Statistics menu, which can also help you identify delays.
Regards, Martin
MartinVisser99@xxxxxxxxx
On 8 January 2012 01:44, Sheahan, John
<John.Sheahan@xxxxxxxxxxxxx> wrote:
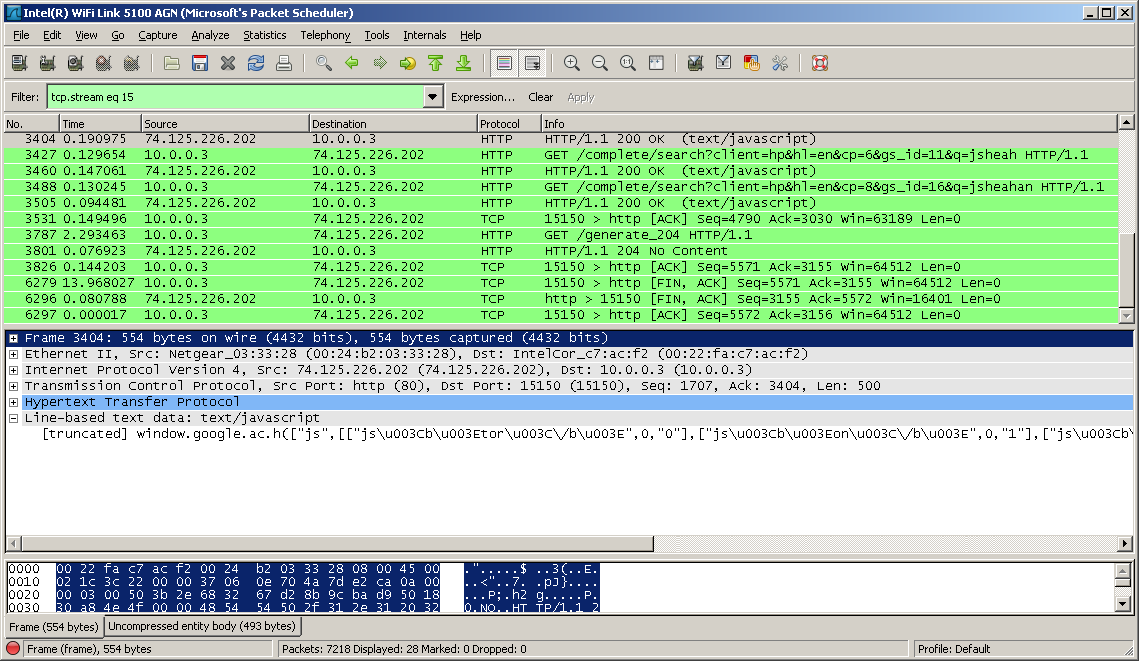
I have filtered out a single conversation and I have the time display set to “Seconds since previously displayed packet”. I want to now add the time field to a graph to show how long it took between packets.
Here is a screen shot of the filtered conversation:
Here is my attempt at adding the Time field for this filtered conversation to the graph which did not work and I’m not sure what I’m doing wrong:
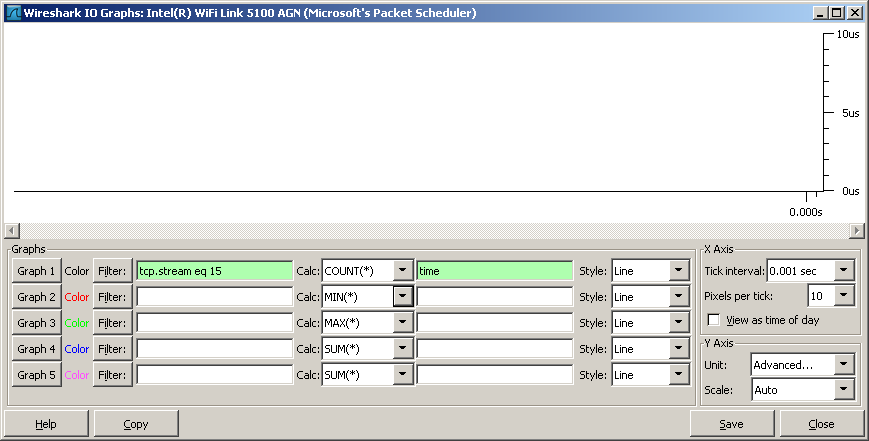
Thanks,
Johnny,
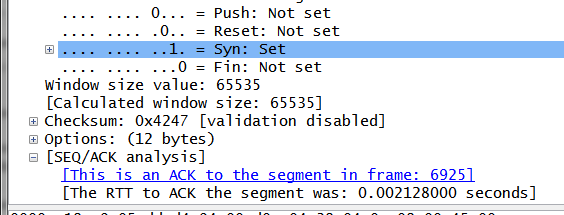
The easiest way is to examine the calculated field "tcp.analysis.ack_rtt". This appears in the details window if you have TCP Sequence Analysis on.
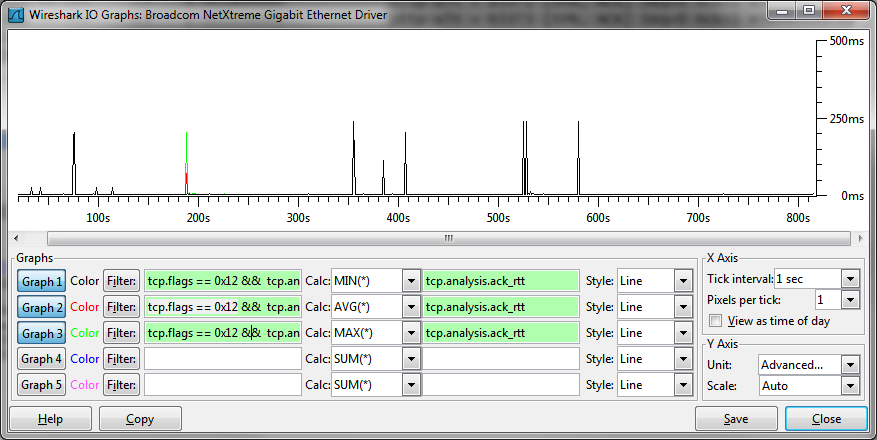
You have to be a little careful when using this though, as Wireshark sometimes miscalculates this in the prescence of Duplicate ACKs. The best way to use it (taking out effects of the server processing delay), is during the initial handshake. So what I do is filter for "tcp.flags == 0x12" (which is the SYN/ACK) and plot tcp.analysis.ack_rtt or add it as a column.
___________________________________________________________________________
Sent via: Wireshark-users mailing list <wireshark-users@xxxxxxxxxxxxx>
Archives: http://www.wireshark.org/lists/wireshark-users
Unsubscribe: https://wireshark.org/mailman/options/wireshark-users
mailto:wireshark-users-request@xxxxxxxxxxxxx?subject=unsubscribe