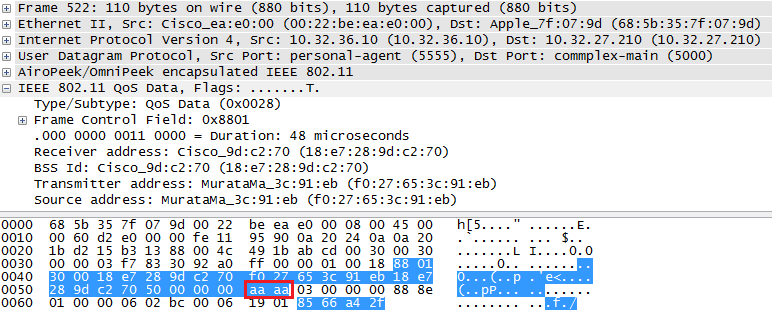
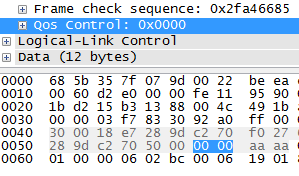
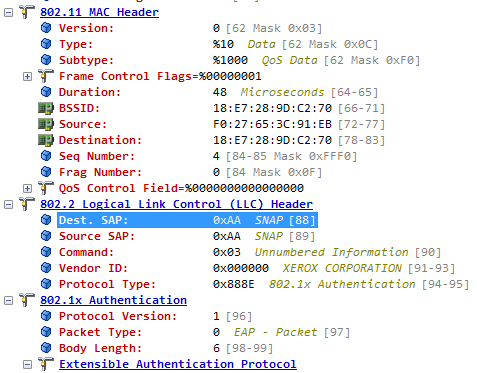
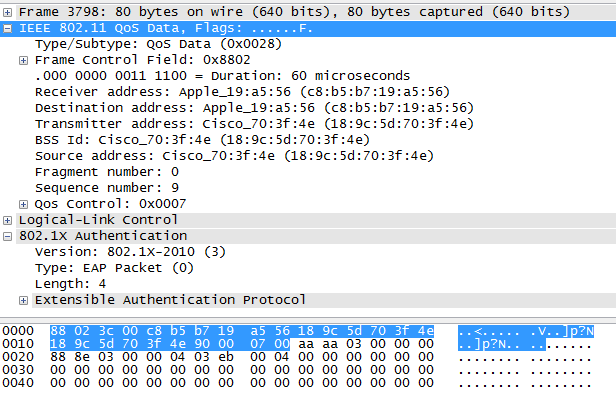
Wireshark-dev: [Wireshark-dev] Wireshark PEEKREMOTE decoding packets from Cisco Sniffer APs inc
- Follow-Ups:
- Re: [Wireshark-dev] Wireshark PEEKREMOTE decoding packets from Cisco Sniffer APs incorrecty
- From: Alexis La Goutte
- Re: [Wireshark-dev] Wireshark PEEKREMOTE decoding packets from Cisco Sniffer APs incorrecty
- Prev by Date: Re: [Wireshark-dev] Byte matching
- Next by Date: Re: [Wireshark-dev] Wireshark PEEKREMOTE decoding packets from Cisco Sniffer APs incorrecty
- Previous by thread: Re: [Wireshark-dev] Is it possible to update the version of gcrypt?
- Next by thread: Re: [Wireshark-dev] Wireshark PEEKREMOTE decoding packets from Cisco Sniffer APs incorrecty
- Index(es):